Mobile Application Penetration Testing
Using either manual or automated ways to examine the application, mobile penetration testing examines mobile operating systems, software, and applications for security flaws. These methods are employed to find potential security holes in mobile applications. Penetration testing is done to make sure the mobile application is secure from threats.
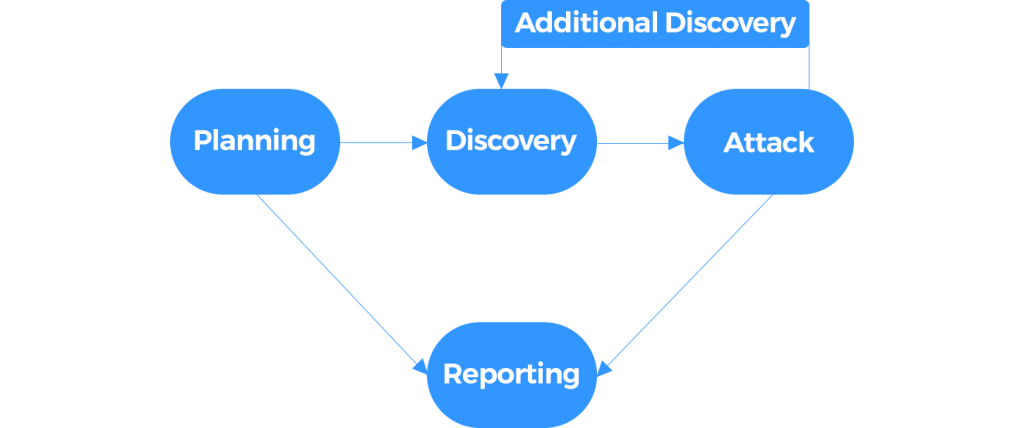
Our Methodology
All testing performed is based on the NIST SP 800-115 Technical Guide to Information Security Testing and Assessment, OWASP Testing Guide (v4).
Contact Us
See How We Can Secure Your Assets
Let’s discuss how Shift Security can solve your cybersecurity needs. Give us a call, send us an electronic mail, or fill out the contact form below.
Electronic Mail: [email protected]
